From a tactical DDoS mitigation standpoint, considered one of the key techniques you must have is sample recognition. Having the ability to spot repetitions that signify a DDoS attack is happening is essential, especially in the Preliminary stages.
Secure your Business online Cyberthreats like DDoS assaults and malware can harm your internet site or on the web support, and negatively have an effect on functionality, shopper believe in, and revenue.
Evaluate the success within your defense system—which include managing apply drills—and ascertain next actions.
Other dispersed denial-of-service assaults are economically inspired, like a competitor disrupting or shutting down One more business's on line operations to steal business enterprise away Meanwhile.
OnePlus is ditching the Inform Slider for an apple iphone-style customizable button - and I’ll be sad to check out it go
This type of attack can fundamentally shut down your web site and also other facts devices. An application-layer assault entails particularly concentrating on vulnerabilities in frequent purposes which include Windows, Apache, or your Internet server.
Some attacks are carried out by disgruntled people and hacktivists attempting to consider down a firm's servers simply just to produce a statement, rejoice by exploiting cyber weakness, or express disapproval.
DDOS means Distributed Denial of Service and is also one of the most cumbersome and troublesome attacks that is comparatively tough to protect versus simply just as a consequence of its nature. A DDOS attack includes mind-boggling a server’s bandwidth potential by using a number of proxies at the same time to mail traffic to the server.
Illinois legislators considers new Monthly bill to limit the scope of waivers for students with disabilities
Should you suspect your community is below attack, it’s significant which you act speedy—in addition to downtime, a DDoS assault can go away your Firm vulnerable to other hackers, malware, or cyberthreats.
Fashionable program options will help identify opportunity threats. A network security and checking provider can warn you to program improvements so as to respond web ddos rapidly.
The actual administrator is generally significantly faraway from the botnet or C&C server, plus the network site visitors is usually spoofed, typically producing detection challenging. The C&C operator then troubles instructions to govern network solutions and gadgets to make the DDoS attack.
Zero-times are your networks unknown vulnerabilities. Keep the possibility of exploits minimal by Studying more details on identifying weak spots and mitigating attack destruction.
DDoS is more substantial in scale. It utilizes thousands (even hundreds of thousands) of related gadgets to fulfill its goal. The sheer volume of your devices employed would make DDoS Substantially more durable to fight.
 Tony Danza Then & Now!
Tony Danza Then & Now! Judge Reinhold Then & Now!
Judge Reinhold Then & Now! Keshia Knight Pulliam Then & Now!
Keshia Knight Pulliam Then & Now! Hailie Jade Scott Mathers Then & Now!
Hailie Jade Scott Mathers Then & Now!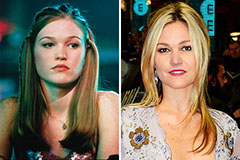 Julia Stiles Then & Now!
Julia Stiles Then & Now!